Abstract
Social engineering is based on the characteristics of humans. There are many famous people who gained notoriety through social engineering, which are briefly presented in this work. In addition, the security objectives of IT security are discussed briefly. Afterwards, the human characteristics that the social engineer uses to achieve this are discussed. Manipulation and influence are in the foreground. But other techniques such as tailgating, reverse social engineering or pretexting help the social engineer to reach his goal. The social engineer eliminates the protection goals of IT security. In order to survive the attacks of a social engineer, good awareness-raising measures are required.
Introduction
Each of us is raised with social engineering. And each of us is a social engineer ourselves. Each of us is manipulated or influenced in the course of his life. However, this usually happens in the personal environment. In education, negotiation techniques or training methods. Likewise, everyone uses social engineering techniques themselves to get to the desired goal. This becomes difficult when it is used due to negative intentions such as industrial espionage or phishing.Each of us is raised with social engineering. And each of us is a social engineer ourselves. Each of us is manipulated or influenced in the course of his life. However, this usually happens in the personal environment. In education, negotiation techniques or training methods. Likewise, everyone uses social engineering techniques themselves to get to the desired goal. This becomes difficult when it is used due to negative intentions such as industrial espionage or phishing [Wes08].
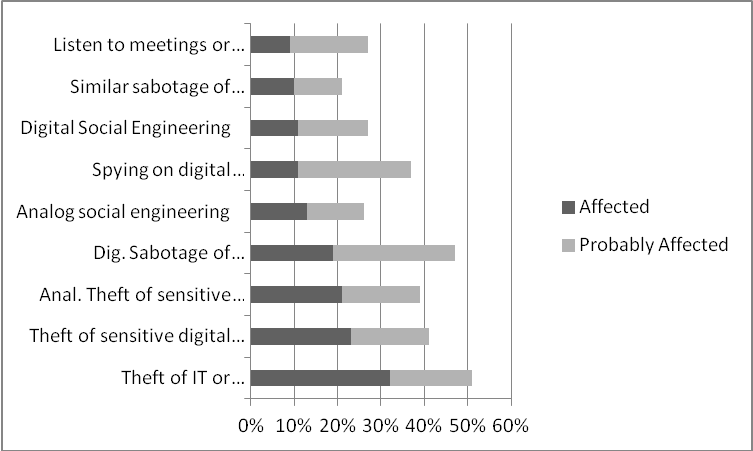
In a survey conducted in 2018 (Figure 1), 13% of companies said they had had incidents of analogue social engineering. The same number stated that they were probably affected. 11% of the companies surveyed said that they were affected by digital social engineering. And already 16% said they were probably affected [Bit18]. Why this is so difficult to assess is explained below in this paper.
Famous Social Engineers
The list of social engineers is long. In 1998 Kevin Mitnick got a sentence of three years because of he used the abilty to deceive. He used social engineering techniques to get into the NSA headquarters without hindrance. Kevin Mitnick achieved this through clever social engineering. While in prison, he wrote the book “The Art of Deceprion” [Lar08].
Another very famous social engineer is Frank Abagnale. He was a good actor and perfected social engineering techniques. He pretended a pilot, lawyer or a professor of a college. When the police catched him in france in 1969, he work for the FBI as a specialist in social engineering crime. About I exploits he wrote a book named “Catch Me If You Can”. A movie under the same name based on his life. Other known social engineers are the Badir Brothers. They used social engineerin techniques to get money from different victims. They get 44 setence because of phone fraud, data theft and pretented to be police officers. Alls of the three brothers were blind. The used their excellent hearing, the ability to prentend other people and programming skills [Wat14].
What Is IT-Security?
IT security is to take measures to protect the confidentiality, integrity and availability [Die04].
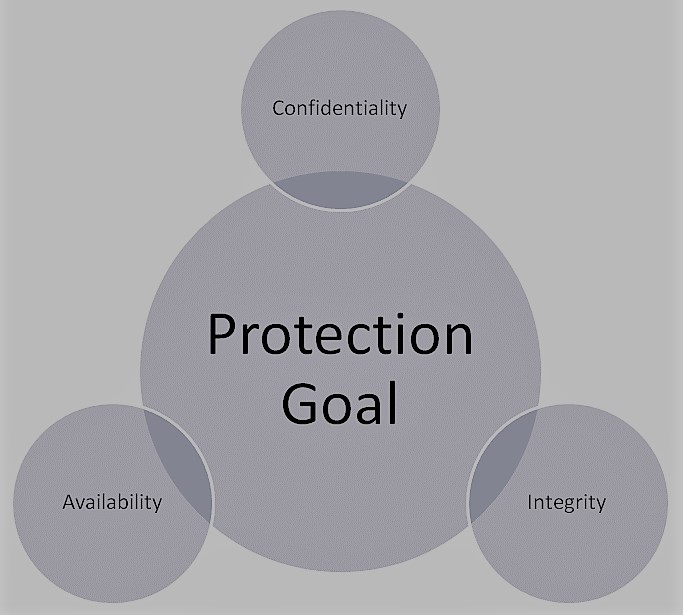
For this reason, they must always be considered together.
Table 1 briefly describes the individual goals as an overview.
| Protection Goal | Description |
| Confeidentiality | Unauthorized information gain |
| Integrity | Unauthorized modification of information |
| Availability | Unauthorized impairment of functionality |
The availability of an IT system or an application is secured if it can be fully used by the user. The user can use data and the complete functionality of the system.
Another protection goal is the integrity of the data. This means that the data must be correct at all times. The data may not be altered without authorization during use and during the query.
Confidentiality is about the fact that information is only available to a legitimate group of people. Helpful here can be to encrypt the data or to provide a password.
These individual protection goals serve to determine the IT security requirements [Gad17].
What Is Social Engeneering?
The most critical secrurity breache is the factor human. But a lot of people think they have to protect about internet hacking or malware. All technical security are useless when the user ignore them. The reason is: convinience [Bla19]. Social engineers take advantages of this. They use different techniques to influence people. They appear with the later victims under a different identity [Fox14]. Social engineering is not only an attack with technical devices, it´s an social attack. From human to human [Sti18]. In times of social networks and other digital networks, social engineers have an easier time. They can use the public information of their victims to attack them [Fox13].
Kevin Mitnick reiterates that soical engineering is the best way to get the data or information you need. He justifies this by saying that technical security mechanisms are much more difficult to overcome than the social component [Hos15].
Kevin Mitnick presents the approach of the social engineer as follows [Gha18]:
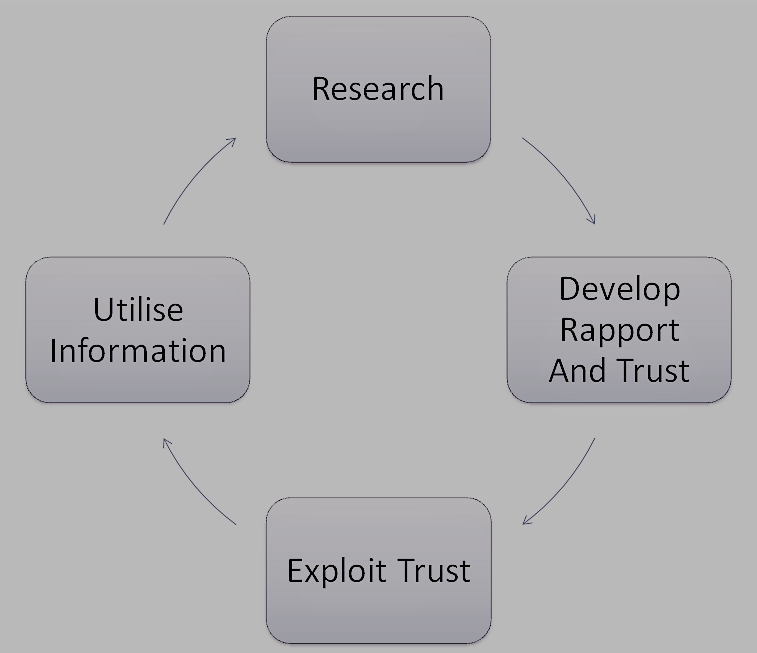
First and foremost, social engineers collect information about their future victims. In the next step, the social engineers develop a trust, as well as a relationship with the victim. Once the trust has been built, this will be exploited. For this purpose, the information collected in the first step will be used in the next step. The approach that Kevin Mitnick has designed is an iterative process. The social engineer collects new information over and over again and more and more solidifies the trust of the victim. He also exploits this from time to time, in which he repeatedly uses the newly gained information against the victim.
Typical characteristics of a social engineer are [Lar08]:
- Good manipulators
- Can confuse you well
- Can put you under pressure
- Good actors
As already written, social engineers can manipulate well. They use many effective techniques to manipulate (Figure 4) their victims [Sti18].
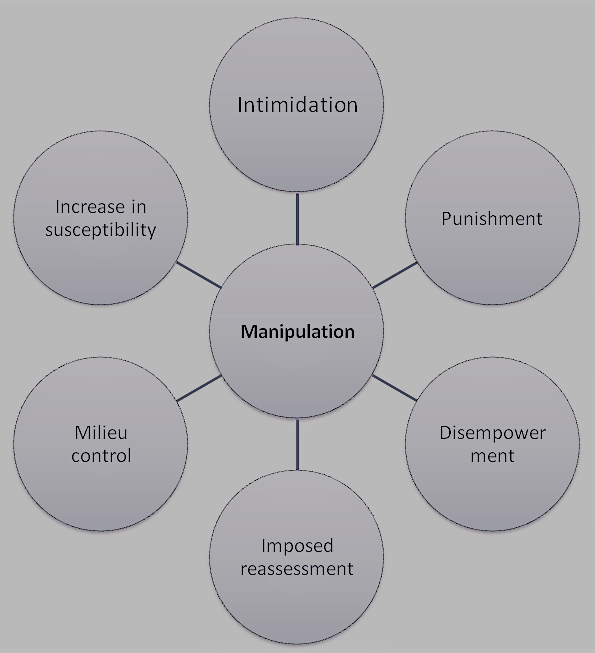
- Intimidation:
This is about creating fear by simply threatening punishment.
- Punishment:
The victim does not want to fear any negative consequences, which is why it follows the instructions.
- Disempowerment:
Social engineers often generate great authority, which they can convincingly play to their victims. This causes the victim to faint, so that it follows the request of the attacker.
- Impossed reassessment:
The social engineer manipulates the victim, for example, by threat, so that it is unsettled and rethink the decision.
- Milieu control:
The social engineer will also nest in the victim’s environment. This can be both private and business. So is closer to his victim and can pursue his goal.
- Increase in susceptibility:
To achieve the desired goal, the social engineer does everything and leaves no stone unturned to bring the victim so far the desired.
Social engineering mainly takes place on a psychological level [Hos15]. Social engineers use typical behavioral patterns that are exposed to every person in their daily social environment. These are deeply rooted in a person, because they are given in the education with on the life path. These are as follows [Fox13]:
- Experience: If no damage occurs in a certain act (even imitated), it is repeated
- Sympathy: People who are more sympathetic to themselves, wishes are more likely to be fulfilled. Also, this is given more faith.
- Authority: If regulations apply, they will be respected. However, this only applies as long as they are complied with by the author.
- Consideration: If there is a debt, then you are more likely to do a favor.
- Time pressure: When a thing has to be done to a certain, rules like to be broken.
In addition, social engineering is also favored by quite normal, desirable properties [Fox14]:
- Helpfulness
- Courtesy
- Friendliness
But social engineers can influence their victim very well. Through this influence (Figure 5) on the victim, the social engineer can get the desired information [Sti18].
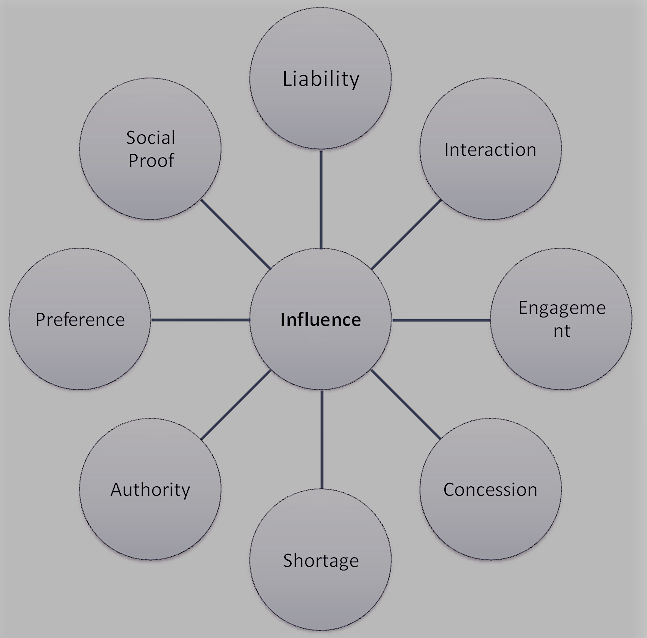
- Liability:
Social engineers use the influence of liability. A victim will not deviate from a beaten track, so if he has already made a payment to the social engineer but is not yet aware that it is one, he will make further payments. Even the social engineer acts binding, in which he gives his victim confidence.
- Interaction:
In order to obtain information, a social engineer does not shy away from offering his victim first, either in words or with a good. The victim then feels compelled to give something in return, it feels in his debt.
- Engagement:
The obligation is an appeal to the victim. Here often the so-called „grandson trick“ is used. The social engineer pretends to be someone from the circle of acquaintances and need help. Because of the appeal to the emotion, this manages to influence the victim.
- Concession:
This influence is often preceded by other influences. As soon as the social engineer has been able to convince his victim, it is hard to get rid of him. An example of this is that if the social engineer manages to enter the house by influencing him, then it is difficult to get rid of him without his having fulfilled his real purpose.
- Shortage:
Here it is suggested to the victim that there is only a limited amount available, both in terms of time and quantity. On the one hand the interest should be increased and on the other hand the interaction should be expanded.
- Authority:
With authority, a great influence can be created. So social engineers like to deceive authority figures. They pretend to be policemen or bosses. Power can be generated with authority.
- Preference:
People tend to help other people who are similar to themselves. This phenomenon is used by social engineers. They find out what preferences, quirks or behaviors the victim has to be like this. For example, they reflect the behavior of their victims.
- Social Proof:
Here, the victim is given a generality of different behavior. The social engineer makes it believable to the victim how he should behave in certain situations, which behavior is the right one. The victim does not want to behave wrong, which is why it gives the faith. This is how the social engineer is able to influence the victim for his own purposes.
Techniques of Social Engineers
In the previous chapter, the characteristics of a social engineer were explained in detail. The main focus was on manipulation and influencing. These properties, which can be used in any human being, can be specifically used to make social engineering attacks. These features are usually associated with various social engineering techniques.
This chapter describes each technique in more detail. A section is shown in Figure 6. In addition to the phishing, elicitation and identity theft shown in Figure 6, the chapter also describes in detail the pretexting, baiting, tailgating, dumpster diving, shoulder surfing and reverse social engineering. It also describes software and mobile applications that can be used for social engineering.
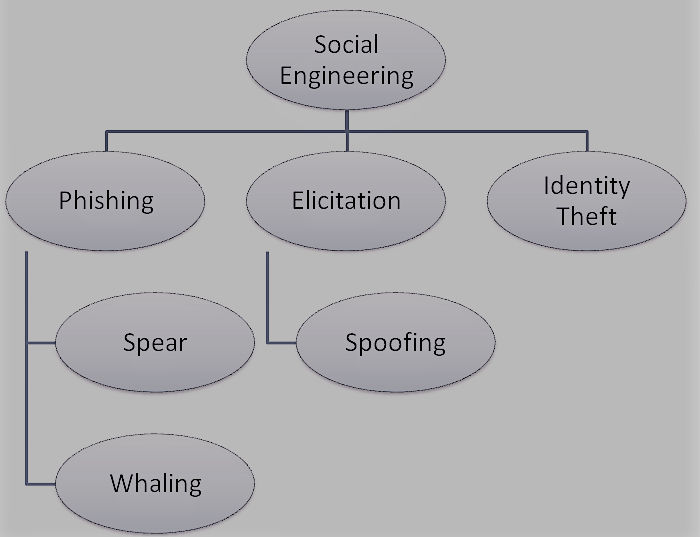
Phising
Phising is the most used social engineering technique. Very often social engineers use this as well as a financial institution, but other companies are also possible [Rao14].
When spear phishing the victim is addressed directly, for example by mail. If this contact contains even more detailed details on the victim this is also called apear phishing [Sti18].
As with all social engineering techniques, here too an exceptional situation is faked. The person being attacked is informed by e-mail [Fox14]. The received e-mail looks identical to that of the real company. Among other things, logos of the supposed company are used. This gives confidence to the victims, which is why they click on the link provided [Rao14]. This link should click on the victims under an excuse, for example, due to an incident, this person has to re-register or data has to be checked. In doing so, the victim has to give out the data for identification or self-certification. These are user data and passwords The goal of this approach is for the victim to initiate a transaction for the social engineer either directly or indirectly [Fox14].
In such an attack, the following points are simulated [Rao14]:
- Due to a server crash, the victim has to reset his password
- From the victim’s account, suspicious transactions have been verified and therefore the credentials need to be verified
- An inadvertent transaction must be made, which is why the credentials must be entered
A special variant of phishing is whaling phishing. Here, under the pretext of an authority person, for example as CEO, an e-mail to the victim with the intention to get company data [Rao14].
Pretexting
At Pretexting, social engineers invent well-thought-out lies. With these lies, they come in contact with their victims. The lies they use as an excuse to build the contact. This is often done step by step until the goal is reached [Rao14].
But Pretexting is more than a simple lie. The social engineer is even a good actor in this case. In order to reach the victim a pretext is sought. The social engineer uses the manipulation, but also influence on the victim. For this purpose, it mainly uses gestures and facial expressions of the victim. As a result, the social engineer quickly gains the trust of the victim.
In addition, the social engineer also uses the following points [Had10]:
- The social engineer collects as much information about the victim as possible
- The social engineer also uses his own interests to inspire confidence in the victim by disclosing his own private information.
- The social engineer uses dialects, often imitating the dialect of the victim
- The simpler the social engineer holds the pretexting, the greater the success
- The Pretexting attack should look like it’s spontaneous, so the malicious intent of the victim is not apparent
- The social engineer has a conclusive answer for contacting the victim
Elicitation
The second largesest method of social engineering is elicitation. In elicitation, the attacker contacts the victim directly by phone. The effort in this method is quite low, also technical means are not needed. Often, however, the so-called spoofing is used here. This allows the transfer of another phone number. This allows you to play another identity. Often this is misused to create authority. Social engineers often present themselves as helpers. Especially in the private sphere, the callers often act as political co-workers and accordingly transmit the emergency number. The victims are told that their money in danger and in the current location is no longer safe. The money would be safer with the police. For that, they would send someone to pass the victim then the money [Sti18].
In some cases, social engineers pretended to be bosses (CEO). They called the accounting for mony transfer. In larger companies, employees often do not know each other. Let alone the boss (CEO) or his voice [Bla19]. The social engineers receive their executive information either directly from employees or from the company website. Many companies publish contacts on their website, sometimes even including a photo. So it is easy for the attackers to impersonate another department and to build trust [Hos15].
Another scenario is to get a call from an unknown. This one knows a lot about one. About the work, about hobbies, etc. The inner skepticism flies, because a certain confidence is built up. The caller pretends to be a headhunter. In the course of the conversation he wants to find out more about one. To be able to use this later for his attack plans [Lar08].
Baiting
But social engineers also use the curiosity of their victims. The so-called Baiting is an Methode, which aims exactly at this property of the victim [Rao19].
When baiting the bait are laid out to the victim. Sometimes this bait is also called honey biscuit. This is set up to harm the victim [Row16]. Social Engineer uses USB drives, CD, DVD or other physical storage media on which malicious software is installed. These storage media placed the social engineer in the company. Popular places are, for example, the toilet or the corridor. The victim who finds the storage medium suspects behind this no malicious attack. This one wants to find out what’s on it. When connecting to the computer then the malware is installed [Rao14].
Another reason why the victim will connect this to the PC after finding the storage medium is that the owner wants to find out. It is precisely this curiosity, but also the satisfaction of being able to hand over the medium to the owner, that is the aim of the social engineer. This will allow the actualization of the malware. Because not the malware is the Instrumentum, so social engineering, but the exploitation of curiosity [Kou19].
Software Tools And Mobile Applications
In some cases, social engineers also use technical means. In the corporate world, mobile applications are playing an increasingly important role. This also offers social engineers new attack surfaces. Many companies may use their own devices, such as smartphones or tablets, as work equipment. These then use to retrieve e-mail, access company data in the cloud, or use messaging services such as whatsapp. Especially with the massaging services, the social engineer can fall back on the spoofing technique. The victim is suggested that the attacker is a colleague to send fake messages and thus get to desired information. Social engineers also steal entire user accounts. The fact that many smartphone applications often require significant access to other data, a complete data theft is very easy. In some cases, the social engineer also deceives the victim with imitation software.
For example, in 2016, social engineers sent a message to an Arab human rights activist with a link to his iPhone. In the message was played with the emotions of the activist. There was talk of human rights abuses. This psychological manipulation of the addressee aroused interest. After clicking on this link a trojan named Pegasus was installed. This exploit a vulnerability of the iPhone. The Trojan copied the entire contents of the iPhone. Apple then closed the vulnerability. However already in mid-2018 a customized version of Pegasus caused a new sensation [Rog18].
Identity Theft
Identity theft is one of the oldest method to deceive other people. But humanity is not even alone. The animal kingdom takes over the identity theft. For example the chameleon or peacock use it to affect their enemy. Identity theft works mainly by influencing. Through the appearance, that is through gestures and facial expressions, but also the linguistic style, trust and authority can be achieved. Fake employee badges, ID card or uniforms can further reinforce this [Sti18].
In addition to the already mentioned properties, which a social engineer assumes when he commits identity fraud, he also likes to use data from real existing people. For example, many social engineers use birth data, social security numbers, addresses, or bank accounts from other people without their knowledge. These data are used by the social engineers to build trust and get to their desired destination [Had10].
Tailgating
Another option that social engineers use to achieve their goal is tailgating. In this variant, the attackers get into the building in the access controls leverage. To do this, wait for company employees to enter the building. The social engineers go directly, as long as the door is still open. Employees think that this is a normal employee. Oftentimes, social engineers also fake extra employee IDs [Rao14].
Two variants of tailgating can be distinguished [Mer09]:
- The social engineer goes through the security check with an authorized person.
- The Social Engineers takes advantage of the sympathy and helpfulness of the victim and offers it for access
Both are usually done on the pretext of being an employee.
Dumpster Diving
In dumpset diving, the social engineers are looking for physical waste. This can be in the private sphere as well as in companies. It searches for discarded sensitive data or information that is no longer needed by the victim and is considered useless. For social engineers, however, this data often means access to additional data. For example, through discarded bank details or carelessly disposed passwords [Kro13].
Dumpster diving is rummaging around in the garbage. Social engineers are not too worried when it comes to obtaining information in trash. Under an excuse, they gain access to the building to look for discarded documents in the garbage cans. Partly, they also gain access by bribing cleaning staff [Hos15]. We also like tailgating. Tailgating allows the social engineers to enter the building, allowing them to look for discarded information in the garbage cans without being disturbed [Rao14]. Another method is to look for information in the garbage bins in front of the building. Many employees inadvertently throw confidential company data or customer data in the bin. Documents are often not shredded beforehand, which is why it makes the social engineers easy in their work [Hos15].
Shoulder Surfing / Hacking
Shoulder surfing or hacking was a very simple variant of social engineering in the 1990s. At that time it was mainly used at telephone booths or cash machines. The spying of passwords, for example, someone with increased user privileges is not uncommon [Lon18].
Shoulder surfing has become increasingly difficult in recent years. Shoulder hacking is more difficult to do after studying without being recognized. Only with additional technology, such as a video camera shoulder hacking can be implemented well. For this reason skimming is often used for social engineering techil shoulder hacking. In this case, for example, the magnetic strip is copied at an ATM. At the same time, the input of the PIN is filmed with a video camera [Kur15].
Good places for the social engineer to exercise shoulder surfing are not only the airport’s main contention area, but also bars, cafes or public spaces that are cozy and where Wifi is available. This availability increases the use of laptops. Clear and bright screens let you spot sensitive information, contacts, emails, or user data [Lon18].
Reverse Social Engineering
In reverse social engineering, the attacker does not contact the victim directly. This is more in a kind of passive attitude. They try to make the victim contact the attacker. This can be done, for example, by asking the victim for help [Kro13].
The attacker first manipulates a system and later offers himself as an expert to solve this problem. This allows the social engineer to gain confidence in the victim and use it for later attacks [Kou19].
There are three possible approaches to social engineering. On the one hand the sabotage and on the other advertising and the support. All three variants can be used simultaneously. So the social engineer can first manipulate a system or an application and later offer its support. With this support, the social engineer can tell his victim to follow his request to fix the problem. The victim will be asked by his credentials, such as the password. This is usually done under a pretense This intent can be, for example, that the password is needed to solve the problem [Kro13].
Almost a decade ago, the importance of social networks such as Facebook, Twitter or similar rapidly increased. At that time there was a growth of about 3% per week. And even today, social networks have not lost in importance. Many users reveal a lot of personal information in the social networks. This information uses social networks like Facebook to offer suggestions to the user. Especially as regards the suggestions of new friends, this poses a danger. Facebook, for example, suggests friends of friends or potential friends with the same interests. Studies have shown that there is more trust in friendships on social networks than in real life. The social engineer uses these friend suggestions from Facebook to use reverse social engineering. In this case, the social engineer does not actively approach the victim, but waits for the victim to report itself to the attacker and send a friend request. At the same time, he makes his profile attractive in order to provoke a contact request. Once the victim has served, the social engineer strikes. As soon as a conversation comes up and thus a trust is created, the social engineer sends the victim a link, which he should click on. This link hides either malware or phishing sites. The social engineer uses the technique of pretexting [Hol11].
Assessment
Assessments are used to uncover security gaps in the company. Within this assessment an example scenario is demonstrated. The moment and the time should be chosen correctly, because this review can take a lot of time. For this reason, you should do such a check at times when the daily business is less [lar08].
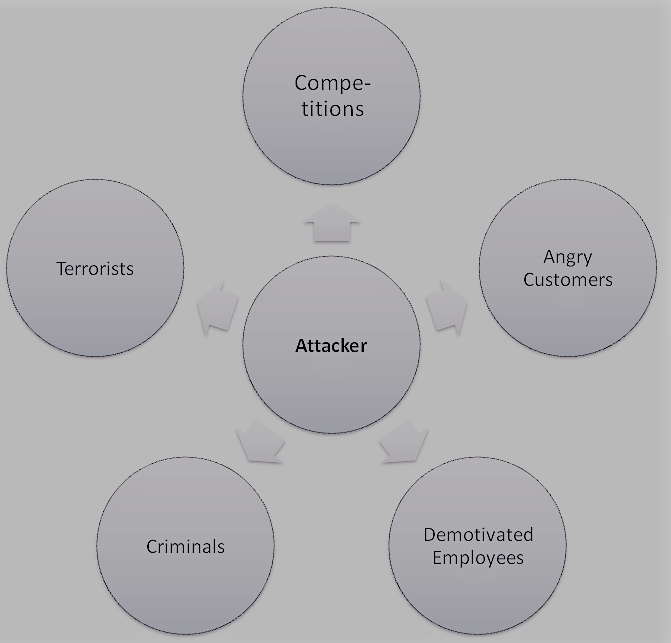
Figure 7 shows which side is where the most attacks on a company come from [Lar08].
Many social engineering attacks come from competitors. Through industrial espionage, they want to harm their immediate competitors. But not always the direct damage in the foreground, but also the mere gathering of information for your own benefit.
Other social engineering attacks come from their own customers, but even former customers may be among them. Most of these are angry customers who want to reduce their frustration with it.
Many companies often have demotivated employees. The demotivation can have different reasons. They let their frustration and anger run wild by sabotaging the business. By doing so, they may cause significant harm to the company.
In contrast to the social engineering attacks mentioned so far, the motive of criminals or even terrorists is often not based on their own personal interests, but mostly different. They use conscious but also unconscious social engineering techniques to achieve the desired goal.
Awareness
Before countermeasures can be taken, this must be anchored in the minds of the employees. Above all, this is the motivation why it is important to protect yourself.
This is best achieved by developing a culture of direct living. In order to make the dangers of social engineering comprehensible to the employees, theoretical training measures are not entirely effective. This is best to revive this with practical examples and interactive (role) games [Hos15].
Possible awareness measures for companies include the layout of checklists. Especially under time pressure many employees can be tempted to answers that they would not have called better. But not all scenarios can be illustrated with checklists, because not all are always known. Here it is more important to change the communication style of the company and the corporate culture. It must also be allowed to ask questions if the employee perceives a request as a security risk. A security expert in the company is suitable for this purpose [Wes08].
Especially with phishing emails, you should not rely exclusively on the firewall. In companies, employees and individuals should be alerted to the fact that they check beforehand whether they really have requested a mail from the sender and expected. Again, you should ask more if the sender has sent you an e-mail. Only when confirmed, should attachments or links be opened [Rog18].
It does not matter if it concerns company data or private data. Sensitive data must be protected. Employees or people who deal with data must be educated, sensitized and referred to the possibilities of social engineering [Fox13].
That’s why a good safety program in a company requires employees to be educated and sensitized. For this round, the following additional measures should be included in this safety program [Kum13]:
- It must be clearly communicated to each individual employee how Phising Fraud works. It helps if you pay attention to how many employees would click on a sent link.
- The help desk should receive a checklist with clear instructions on how to respond in the event of a password request. These guidelines should be followed when an employee logs in if they forget the credentials.
- In order to prevent tailgating, technical measures as well as the awareness of the employees should be sensitized. This should be done tests in which an unknown person follows an employee.
Awareness measures can not be expressed in monetary units. It’s hard to calculate this. Since this can not be expressed in numbers often the necessary Awareness measures are not taken into account. The ROSI (return on security investment) is impossible to calculate [Sch07].

In order to avoid the introduction of a social engineer in the company, it is advisable to consider the following points in figure 5 [Hos15].
In a company It is not always possible to know every colleague or employee, for this reason it makes sense to distribute employee ID cards. It is advisable for visitors to issue visitor badges. This immediately indicates who this person is. However, visitors should never be left unattended on the premises to avoid spying or unauthorized use in locked rooms. If an unknown person is in the building or you should find a person without a passport, then this person should be addressed directly. When contacting them, they should find out why they are in the building or on the company premises. if necessary, this person of the place should be referred. Systems, such as the computer or application software, such as CRM or ERP systems, should be set to require re-password entry after a period of inactivity. In many companies, confidential information is often communicated over the phone. Binding transaction instructions are also accepted among colleagues, often also by colleagues who are not directly acquainted. In order to guarantee the confidentiality of the information, but also the authenticity, it makes sense to agree on codewords within the company or the organization, which are changed regularly. Similar to an RSA token key. also unconscious social engineering techniques to achieve the desired goal.
Conclusion
Above all, social engineering is manipulating or influencing people. Especially in combination with the different techniques, this can lead to greater success. Social engineering is becoming ubiquitous. Especially in education, in the school system or if someone wants something. The fact that the social engineering typical human characteristics are mentioned, such as helpfulness or the like, makes it very difficult to detect malicious social engineering. It only becomes critical here when social engineering is used to harm someone, a person or a company. At the same time, social engineers are not afraid to use techniques like dumpster diving or playing with the feelings of their victims. In order to get a sense of social engineering or to raise awareness, awareness training should be carried out in companies. Through checklists and the awareness that social engineering can be done at any time, attacks can be minimized.
References
[Fox14] Dirk Fox. Social Engineering im Online-Banking und E-Commmerce. Springer Gabler, 2014. [Fox13] Dirk Fox. Social Engineering. Springer Gabler, 2013. [Lar08] Michael Lardschneider. Social Engineering Eine ungewöhnliche aber höchst effiziente Security Awareness Maßnahme. Springer Gabler, 2008. [Wat14] Gavin Watson; Andrew Mason; Richard Ackroyd. Social Engineering Penetration Testing. Syngress, 2014. [Bla19] Bettina Blass. Internetsicherheit: Schwachstelle Mensch. Springer Verlag, 2019. [Sti18] Sonja Stirnimann. Der Mensch als Risikofaktor bei Wirtschaftskriminalität. Springer Verlag, 2018. [Die04] Rüdiger Dierstein. Sicherheit in der Informationstechnik – der Begriff IT-Sicherheit. Springer Verlag, 2004. [Sch07] Klaus Schimmer. Sicherheit beginnt im Kopf. Springer Verlag, 2004. [Wes08] Bettina Weßelmannn. Maßnahmen gegen Social Engineering. Springer Verlag, 2008. [Hos15] Dennis Hoss. Social Engineering – unterschätzte Bedrohung für die Informationssicherheit. Springer Gabler, 2015. [Rog18] Marko Rogge. Professionelle Angriffe auf Smartphones unter Zuhilfenahme von Social Engineering. Springer Verlag, 2018. [Win06] Martin Wind; Detlef Kröger. Handbuch IT in der Verwaltung. Springer Verlag, 2006. [Gad17] Andreas Gadatsch; Markus Mangiapane. IT Sicherheit Digitalisierung der Geschäftsprozesse und Informationssicherheit. Springer Verlag, 2017. [Rao14] Umesh Hodeghatta Rao; Umesha Nayak. The InfoSec. Apress, Berkeley, CA, 2014. [Kur15] Masaaki Kurosu. Human-Computer Interaction Design and Evaluation. Springer International, 2015. [Kum13] Veerendra Kumar; Mukta Bhatele. Proceedings of All India Seminar on Biomedical Engineering 2012 (AISOBE 2012). Springer India, 2013. [Gha18] Ibrahim Ghafir; Jibran Saleem; Mohammad Hammoudeh; Hanan Faour; Vaclav Prenosil; Sardar Jaf; Sohail Jabbar; Thar Baker. Security threats to critical infrastructure: the human factor. Springer US, 2018. [Kou19] Shahram Montaser Kouhsari. Fundamental Research in Electrical Engineering. Springer Nature Singapore, 2019. [Row16] Neil C. Rowe; Julian Rrushi. Introduction to Cyberdeception. Springer Cham, 2016. [Had10] Christopher Hadnagy. Social Engineering The Art of Human Hacking. Wiley, 2010. [Mer09] René Merten. Darstellung der Bedrohung durch Social Engineering und Analyse der als Gegenmaßnahme vorhandenen IT-Sicherheitsprozesse am Beispiel eines großen Unternehmens. Diplomica Verlag, 2009. [Bit18] Bitkom. Umfrage zur Art der Vorfälle von Computerkriminalität in Deutschland 2018. Wirtschaftsschutz in der Industrie, 2018. [Hol11] Thorsten Holz; Herbert Bos. Detection of Intrusions and Malware, and Vulnerability Assessment. Springer Verlag, 2011. [Kro13] Katharina Krombholz; Heidelinde Hobel; Markus Huber; Edgar Weippl. Social engineering attacks on the knowledge worker. SIN ’13 Proceedings of the 6th International Conference on Security of Information and Networks, 2013. [Lon18] Johnny Long. No Tech Hacking: A Guide to Social Engineering, Dumpster Diving, and Shoulder Surfing. Syngress Publishing Inc., 2018.
